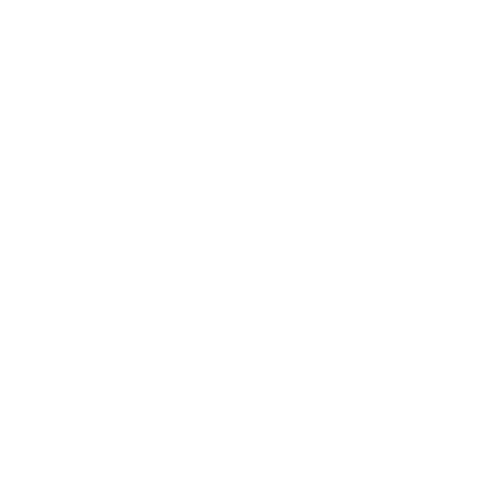
68% of SMEs have never penetration-tested their IT systems.
In addition to our Basic Cyber Security & Health Checks, Black Sheep Support offers a range of advanced cyber security services to further strengthen your business’s defence against evolving threats. While ensuring your organisation has solid foundational security is critical, taking the next step to implement advanced measures is equally important to address more sophisticated risks. Here’s how we help businesses like yours take cybersecurity to the next level:
Penetration testing, or pen testing, is a controlled and simulated cyber-attack on your systems, networks, or applications to identify vulnerabilities before malicious actors can exploit them. Our expert team conducts thorough penetration tests to expose weaknesses in your infrastructure, including:
Advanced Cyber Security Service Testing
External Network Testing:
We simulate attacks from outside your organisation to identify points of entry and weaknesses in your external-facing systems.
Internal Network Testing:
We also test your internal network to uncover vulnerabilities that could be exploited by insiders or attackers who have gained unauthorised access.
Web Application Testing:
We assess your web applications for potential security flaws such as SQL injection, cross-site scripting, and other vulnerabilities commonly exploited in cyber-attacks.
We’re Outstanding In Our Field
Test results are compiled into a detailed report, along with prioritised recommendations to mitigate the risks we identify. Penetration testing helps ensure your systems are resilient against external and internal attacks, giving you the confidence that your infrastructure is secure.
Book a consultation with one of our team to find out how we can help you.

BASIC CYBER SECURITY

ADVANCED CYBER SECURITY

CYBER ESSENTIALS

PATCH MANAGEMENT
VIRUS PROTECTION